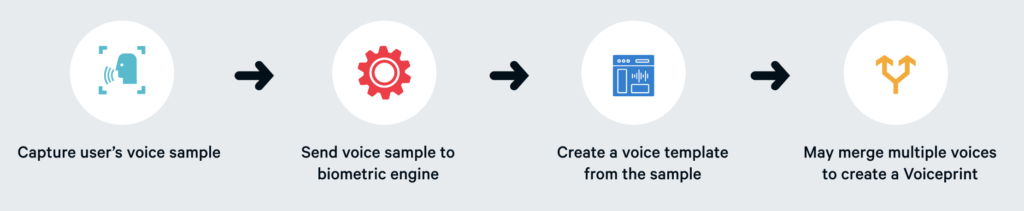
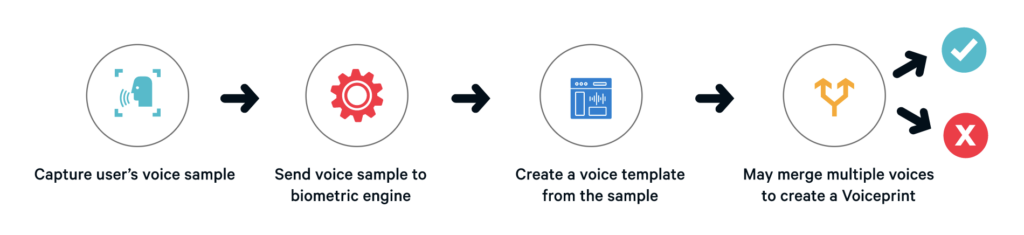
We are often asked how do voice biometrics work. Voice biometrics is the science of using a person’s voice as a uniquely identifying biological characteristic in order to authenticate them. Also referred to as voice verification or speaker recognition, voice biometrics enables fast, frictionless and highly secure access for a range of use cases from call center, mobile and online applications to chatbots, IoT devices and physical access.
Massive advances in neural networks over the past 2-3 years have enabled the development of voice biometric algorithms that are faster, more accurate, and can authenticate users with a smaller amount of speech. In fact, ID R&D is now able to exceed the accuracy of a 4-digit PIN in many use cases.
How does voice authentication work? Like other biometric modalities, voice biometrics offer significant security advantages over authentication methods that are based on something you know (like a password or answer to a “secret” question) or something you have (like your mobile phone). Voice biometrics also improves the customer experience by removing frustration associated cumbersome login processes and lost and stolen credentials.