Biometric Login for Password Replacement, MFA, and Step-Up Authentication
Biometric Login
According to the 2019 Verizon Data Breach Investigations Report, 80% of hacking related breaches are due to compromised, weak, and reused passwords. Passwords provide a broad attack surface with many vulnerabilities. In the midst of increased cyberthreats and fraud, voice and face biometrics reduce risks while offering a simpler way for users to login.
Unlike passwords, PINs, and “secret” questions, biometrics require nothing for users to remember and nothing that can be stolen, “phished,” found on the dark web, or shared.
Is biometric login secure enough?
Today, there are several mature biometric modalities that deliver proven matching accuracy for even the most demanding use cases — from banking to healthcare to government. Biometrics ensure a low risk of the wrong person getting access while liveness detection prevents spoofing attacks. Both are necessary.
Businesses can choose one or more biometrics to achieve a level of security that matches risk. A key advantage is that biometrics almost always offer less effort and less friction and work faster than other approaches like One Time Passcodes — all while offering higher security.
The biometric system produces scores for each authentication attempt. These scores will create a pattern. Where the system is configured to declare a “verified” or “not verified” response results in a distribution between the two types of errors. This distribution is plotted as a Detection Error Trade-off Curve as seen in the figure below. By having more False Reject errors (the y axis), you will get fewer False Accept or “imposter” errors (the x axis).
Of course, the goal of biometric identification and authentication systems is to make both of these error types extremely small, ideally not allowing any impostors through with only a negligible number of valid people getting rejected.
The chart below shows the trade-off between the False Accept and False Reject Errors for state-of-the-art voice and face biometrics as well as the combination of the two.
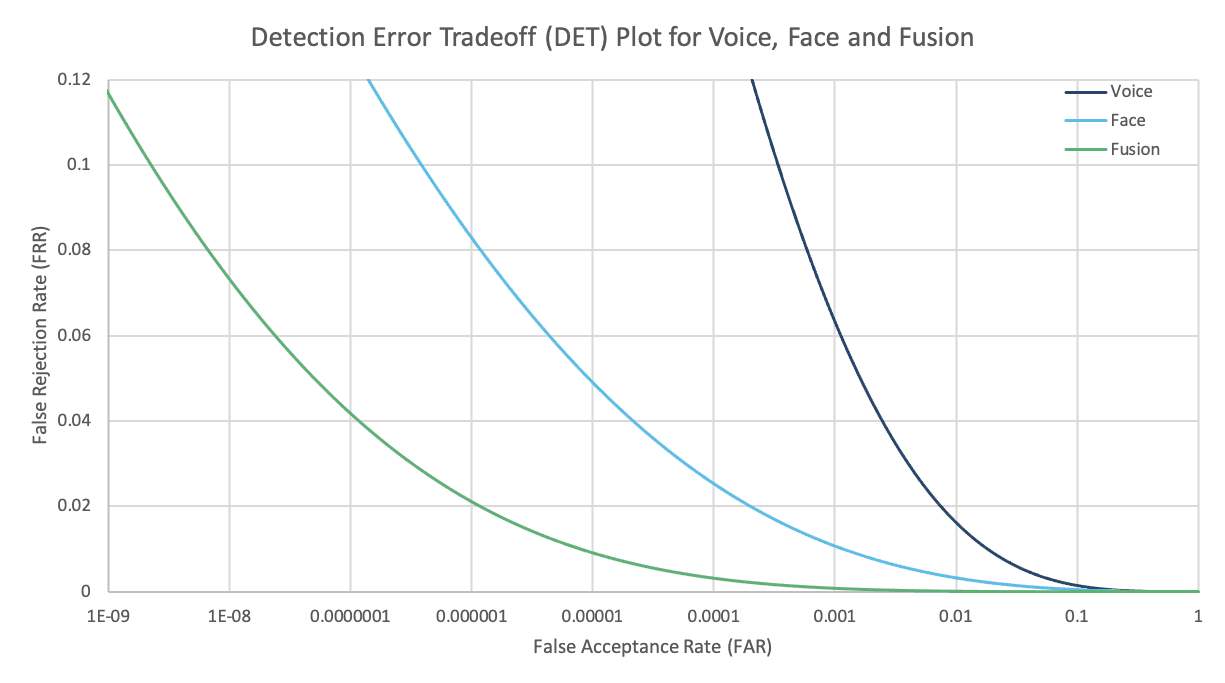
For example, you can see from this chart that when using face biometrics, it is possible to choose an operating point such that the number of False Accepts is 0.00001, which is 1 in 100,000 with a False Reject Rate of slightly more than 0.06, or 6 percent. This is true for any individual attempt.
Additionally, although error rates for voice biometrics alone are higher than face, combining voice and face results is an astounding level of accuracy and as well as a reduction in false rejections of valid people. In practice combining voice and face is easy to do in a mobile app.
Let’s compare these results to the standards for Strong Authentication on Android in which the acceptable False Reject Rate is 10% and the False Accept Rate is 1 in 50,000. Therefore, you can see that the fusion of face and voice presents a far more secure capability than industry standards.
What does this all mean to you?
Using voice and face biometrics on mobile and web devices results in significant security and usability benefits over passwords:
- No need to remember anything
- Works with the camera and microphone on any modern computing device
- Faster, simpler, and more secure than one-time passwords, which are compromised as soon as a fraudster compromises your email or your device
- Immune to social engineering; can’t be sold on the Dark Web
- Prevents credential sharing in the workplace
- Usable across communication channels
- Blocks common fraud vectors, like SIM swaps and device spoofing
Biometrics for Multi-Factor and Step-Up Authentication
Maybe your organization isn’t ready to eliminate passwords just yet but needs to strengthen authentication by adding another factor. Voice or face biometrics can be added as a second factor during login or as a form of step-up authentication when the user is performing a higher risk transaction. Unlike approaches that require users to enter one time passwords and PINs (OTPs), biometrics provides a way to increase security with virtually no increase in user friction.
A step up authentication process can be multi-factor, or it can use a combination of multiple biometrics, such as voice biometrics and facial recognition with voice and face liveness detection to provide an extremely high level of security.
Preventing spoofing attacks with Liveness Detection
When it comes to authentication, biometric data used for matching is stored as an encrypted template apart from a user’s personally identifiable information – usually in your cloud, on your premises, or on the user’s device. This template is meaningless to anyone who obtains it. The real concern is how easily and quickly a fraudster can find your photo, a video, or a recording of your voice online and use it to “trick” a biometric system into thinking it’s seeing or hearing you. This is called a spoofing attack, or presentation attack, and it is prevented using a technology called liveness detection.
ID R&D’s IDLive Voice provides the #1 rated anti-spoofing for voice biometrics. IDLive Face is our ISO 30107-3 compliant passive facial liveness product. Both products work in the background to distinguish between a real person and a presentation attack without any actions or additional effort from the user. Consequently, because the liveness detection is imperceptible to users without indication of when it’s happening or what it’s looking for, it offers no clues to fraudsters on how to break it.
A holistic solution for frictionless Biometric Login
ID R&D’s IDVoice text dependent and text independent voice biometrics offer market-leading accuracy based on our advanced modified x-vector approach for feature extraction technology. The product achieved strong results in the industry’s leading benchmark challenge, the 2019 NIST Speaker Recognition Evaluation, and ranked #1 in the ASVspoof 2019 Automatic Speaker Verification Spoofing and Countermeasures Challenge. Additionally, we offer multiple leading facial recognition solutions for integration with IDLive Face, our ISO 30107-3 compliant passive facial liveness product.








