Types of fraudulent documents
Counterfeits. A counterfeit is a fabricated document, either physical or digital, designed to imitate a genuine or fictitious document.
Forgeries. Forgeries are genuine documents altered by text and font manipulations, portrait substitutions, and false signatures.
Reproductions. These are physical or digital copies of documents created using a copier, scanner, or digital display device like a smartphone or tablet. Although not inherently fraudulent, reproductions can make counterfeit or forgery detection more challenging. Detecting their use in digital IDV is crucial to prevent fraud.
Presentation Attacks in Digital Identity Verification
A document presentation attack is when a bad actor tries to misrepresent their identity by presenting a full or partial document reproduction. Recent ID R&D research indicates that most attacks making use of fraudulent documents are presentation attacks (see figure below).
Despite the prevalence of presentation attacks, most KYC platforms focus on document authenticity (correctness of document structure, text, bar codes) leaving presentation attacks undetected.
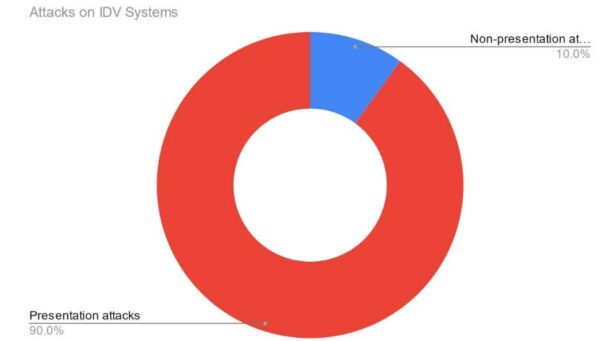
Figure: The majority of attacks on identity verification systems are presentation attacks
Examples of presentation attack methods include:
Printed copy
The attacker presents a physical paper print or black-and-white photocopy of a document to the camera. The attacker can use different techniques (in order of easy to difficult):
- printed cutouts without lamination
- printed cutouts with lamination imitation
- laminated cutouts
- plastic printed forgery

Figure: Printed copy
Screen replay
The attacker presents a digital reproduction of a counterfeit, forged, or stolen document using a device screen, such as a laptop, tablet, or smartphone. It could include the use of a pre-recorded video or image and then presenting that imagery as if a physical document is being presented in front of the camera.

Figure: Screen replay
Portrait substitution (portrait overlay)
The face image on a document is replaced with a different image, such as through physically altering the document by cutting out the original face image and pasting a new one.

Figure: Portrait substitution
The following figure shows the breakdown of document-based attacks on IDV systems according to ID R&D data. Note that a significant majority of document-based attacks on IDV systems are conducted using screen replays, making these attacks particularly important to detect.
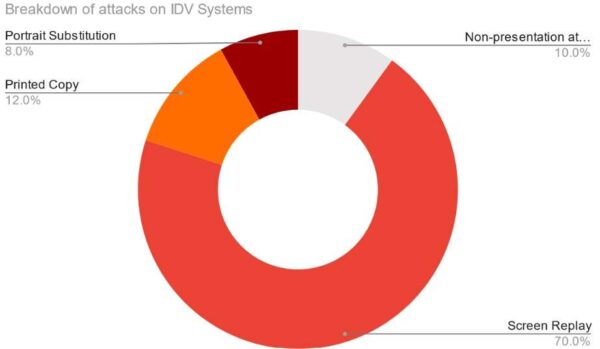
Figure. Breakdown of document attacks on IDV systems.
Mitigating the risks with document liveness detection
Document liveness detection products like IDLive Doc from ID R&D help detect and prevent presentation attacks, including screen replays and other attack types. Desirable features for document liveness solutions include:
- Detecting presentation of printed copies, screen replays, digital snapshots, and portrait substitutions
- Detecting attacks in near real-time without adding friction to the user experience or alerting fraudsters
- Detecting fraud that humans cannot
- Compatibility with all types of identity documents worldwide
- Functioning independently of user experience
- Integration with existing KYC processes without disrupting core components
- Rapid implementation into any remote onboarding system
- Compatibility with Windows or Linux servers
Key Takeaways
Digital identity verification offers considerable advantages compared to in-person processes. However, it also exposes the system to potential fraud, where bad actors may use various document reproductions to conceal their true identities. These reproductions can be full or partial, physical or digital, and original or tampered. Detecting them is crucial for maintaining the integrity of remote onboarding.
Presentation attacks, which constitute over 90% of all document-based attacks on digital IDV, include printed copies, screen replays, and portrait substitutions. Screen replay attacks account for the majority of these attacks, with printed copies also contributing significantly.
Implementing accurate and effective document liveness detection is essential, but it should also be easy to integrate into legacy systems and user-friendly. Legitimate users should not experience unnecessary friction in the form of complicated document capture instructions, failed image captures, or false-positive alert interruptions.





