In 2020 so far, more than 16 billion records including credentials, personal and financial information have been exposed on cybercriminal forums. According to IBM, the average cost of a data breach is $3.86M but many have been far more damaging. For example, the total cost of the 2017 Equifax breach was estimated at $700M and Marriott paid over $200M in damages and fines for their 2018 breach . If these alarming statistics aren’t enough reason for companies to step up their authentication strategies, regulations like the Payment Services Directive 2 (PSD2) in Europe are accelerating initiatives to implement Multi-factor Authentication.
What is Multi-factor Authentication?
Multi-factor Authentication (MFA) is the verification of a user’s identity with multiple credentials for enhanced security. MFA is a popular way to neutralize risks associated with passwords by adding a second, different factor to password-based login. Users today are familiar with two-factor, or two-step, authentication which is a subset of MFA.
While an MFA solution does not have to include a password, it must include at least two pieces of evidence that you are who you claim to be. Likewise, these factors must come from at least two of the three categories of accepted credentials.
Authentication factors fall into three buckets: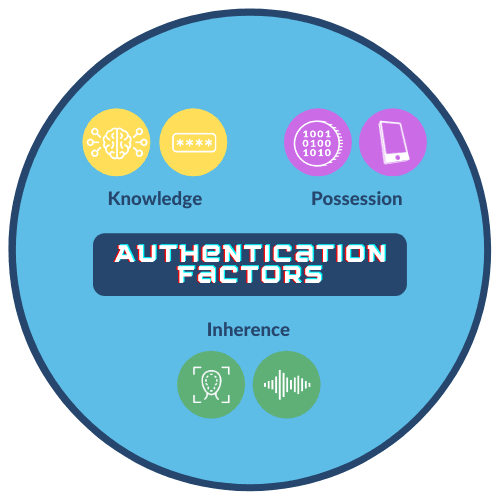
- Knowledge: Something the user knows, like a password or the answer to a secret question.
- Possession: Something the user has, like a mobile phone or laptop, identified using digital certificates.
- Inherence: Something the user is, such as biometrics. Commonly used biometrics include face, voice, and behavioral patterns such as a user’s keystroke.
As consumers we understand the need for authentication that secures our data and accounts. However, we also value speed and convenience – in fact, we might value it a little too much. Multiple surveys have found that the majority of consumers understand the risks yet still reuse passwords across accounts. A new Carnegie Mellon study found that only a third of users change their passwords after a data breach announcement!
Today’s enterprise-grade biometrics provide a highly reliable, independent authentication factor. For example face and voice biometrics are particularly well suited to deployment in mobile applications and conversational interfaces (like chatbots). Whether your business is looking to increase security, improve the user experience, comply with regulations or all of the above, there is a strong business case for deploying biometrics.
5 Reasons to Make Biometrics Part of Your Multi-factor Authentication Strategy
#1 Reduce friction in the user experience
Many approaches to MFA add time and effort to login, making an already process even more frustrating. Face recognition with passive liveness detection offers accuracy that is near perfect and virtually no friction. Users simply take a quick selfie and often even this happens automatically and so fast that it’s imperceptible. Likewise, voice biometrics enable hands-free, low-effort authentication that is easily combined with voice to further enhance security or simply offer users a choice based on their environment.
Enterprise-grade biometrics, unlike the biometrics that are native to the mobile device, are completely independent of the phone. As such, the user’s mobile device can still be used as a “possession” factor. As a result, this form of multi-factor authentication using biometrics offers a highly secure, passwordless user experience.
#2 Fight social engineering and decrease Account Takeovers
Biometric authentication offers stronger security than factors such as knowledge authentication, which is highly vulnerable to social engineering. According to PCMag, Google has seen a 350 percent increase in phishing websites during COVID-19. Beyond phishing attacks that trick people into divulging passwords and account information, hackers are also skilled at using personal details found online or on the Dark Web to reset passwords, hack them, or trick contact center agents into resetting them. For example, the information used to answer “secret questions” like your place of birth or last known address really isn’t so secret. And clever hackers are now taking advantage of those fun social media “quizzes” and chain posts to get another level of information. Keep that in mind next time you divulge the name of your childhood best friend or high school mascot!
Unlike knowledge factors, biometrics are excellent for fighting fraud as they are inherently tied to the user. Even if a customer is locked out of their account or has a new device, their biometric remains a reliable factor for re-authentication.
#3 Clean up the password hygiene problem
Research shows the average user has 70-80 accounts with passwords. And a study by Mastercard and the University of Oxford found that “21 percent of users forget passwords after 2 weeks, and 25 percent forget one password at least once a day.” While it’s no  surprise that password reuse or “recycling” is so common, the damage is staggering. Verizon reports that 80 percent of data breaches are caused by compromised, weak, and reused passwords.
surprise that password reuse or “recycling” is so common, the damage is staggering. Verizon reports that 80 percent of data breaches are caused by compromised, weak, and reused passwords.
Bad password hygiene isn’t just a customer issue. According to Gartner, between 20 to 50 percent of all IT help desk calls are for password resets. These come at an estimated price tag of $40-50 per call. Even worse, password reuse and sharing in the workplace opens organizations up to significant cyber threats – especially when privileged access to administrative or operational accounts is breached.
Using an authentication factor that can’t be lost, forgotten or shared closes security gaps that result in data breaches, while reducing help desk costs and user frustration.
#4 Detect more fraud.
We know passwords can be hacked and personal information used in knowledge authentication is easy to find online. Other tactics like SIM swapping enable fraudsters to intercept one time passcodes that are intended to protect accounts. When successful, fraud may go unnoticed for hours, days or weeks. When it comes to biometric authentication, criminals may use recorded or synthesized voice, printed photos, video replays, and 2D or 3D masks in an attempt to make the system think it sees or hears a match for the real user. A technology called liveness detection protects against these biometric spoofing attacks in real-time to catch fraudsters in the act. Moreover, a passive approach to facial liveness ensures the process keeps friction out of the user experience.
#5 Combine biometrics for even stronger security
Adding a second biometric to an authentication process is a way to “step up” security in higher risk scenarios with minimal if any additional effort for the user. For example, the fusion of voice biometrics and facial recognition results in 100x stronger security than using facial recognition alone. With the addition of voice and facial liveness, authentication is close to impenetrable. While the combination is not multi-factor, it can be combined with a factor like the user’s device to meet criteria for Strong Customer Authentication.
Security experts and organizations including NIST recommend using MFA whenever possible, especially when protecting sensitive data such as financial information and health records. But because breaches to everyday accounts like email can create a “domino effect”, two-factor authentication adoption is recommended across a range of accounts.
A 2019 study by Ponemon Institute found that 67 percent of respondents did not use any form of two-factor authentication in their personal life and 55 percent of respondents did not use it at work. Is this due to a lack of education? Our aversion to adding time and effort to login? It’s probably both. Fortunately, users are becoming more vigilant and biometric authentication introduces a way to strengthen security while reducing user effort.
Why Multi-factor Authentication is Important
In most cases, two authentication factors offer better protection against account takeovers — especially when one of those factors is a password. MFA helps keep accounts secure when one factor is compromised. Additionally, MFA helps some companies comply with regulations for Strong Customer Authentication (SCA). A disadvantage is that it can add friction to the user experience. This is where biometrics provide significant value because they strengthen security without adding time and complexity to the login process. Additionally, implementing biometrics with anti-spoofing is a more secure factor than options such as one time passwords sent via text.
Considering Biometrics for Multi-factor Authentication?
As mentioned previously, it is important to understand the differences between consumer and enterprise-grade biometrics when considering biometric deployment in the enterprise. Only the latter serves as a true authentication factor that is separate from the device. As such, if using an enterprise-grade biometric, the device can be used as a second factor for a simplified user experience. Additionally, an enterprise-grade biometric can’t be “reset” on the device by a user who gains access to a device and it is persistent should a user change their device. We wrote a whitepaper that goes into much more detail on this topic if you’d like to learn more.
